This How-to article is meant to configure Windows Server 2012 Network Policy Server, Certificate Authority with a Cisco WLC 2504 series (with Software version 7.4.100.0)
As specific as that list is, much of what Cisco offers with older IOS versions still holds true. The authentication model still works, particularly the 802.1x configurations. From the get go, you will have to create a new certificate if it’s not a Domain Controller. This link explains in depth creation of a Certificate for use on a PEAP authentication model. If you do have a domain controller, you can use the domain certificate for this purpose.
I recommend creation of a an RAS-IAS certificate and pushing the certificate via GPO, namely as you can change the expiration date of the certificate (like 10 years in the future if you really want).
First, configure the NPS:
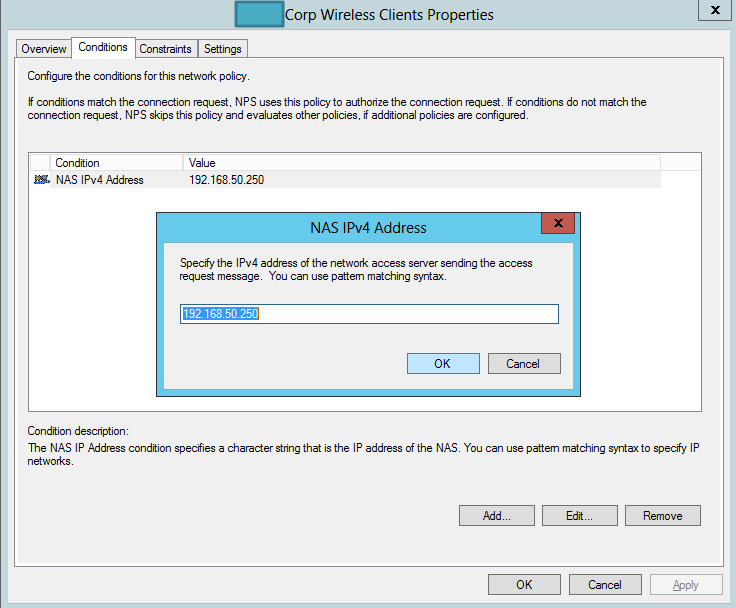
You’ll need the IP address of the WLAN controller (this example is 192.168.50.250) , configure the shared secret as you’ll need it for the Cisco WLAN.
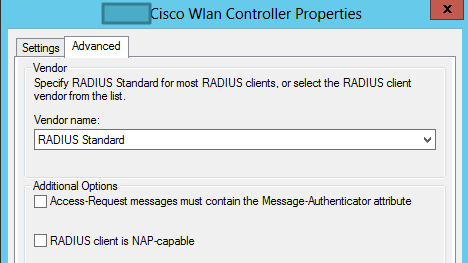
For the properties portion, use RADIUS Standard. You can choose a specific Cisco device – but for this example and setup the RADIUS Standard works.
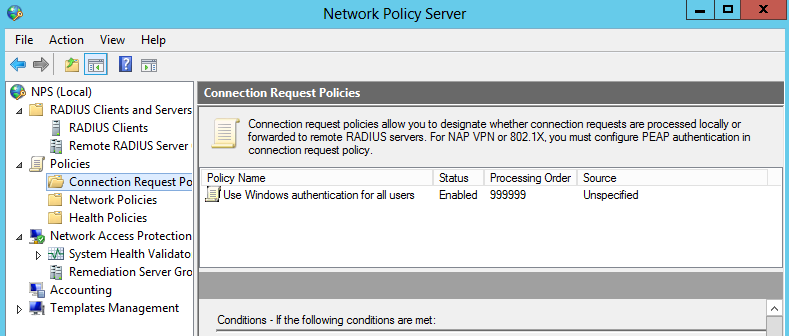
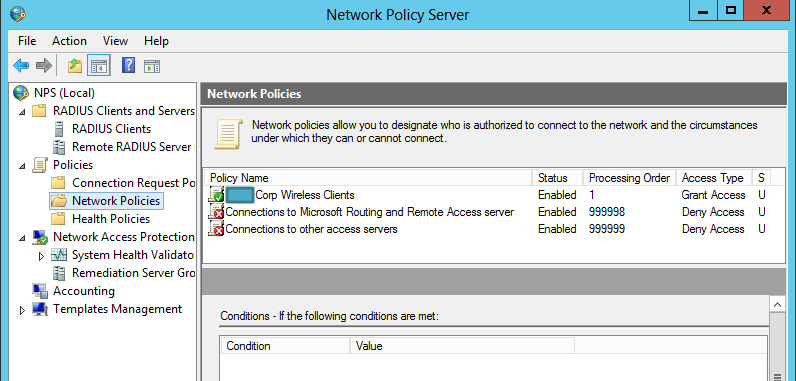
Next, click on Connection Request Policy, we’re going to create a new policy to use this server as the RADIUS authentication server
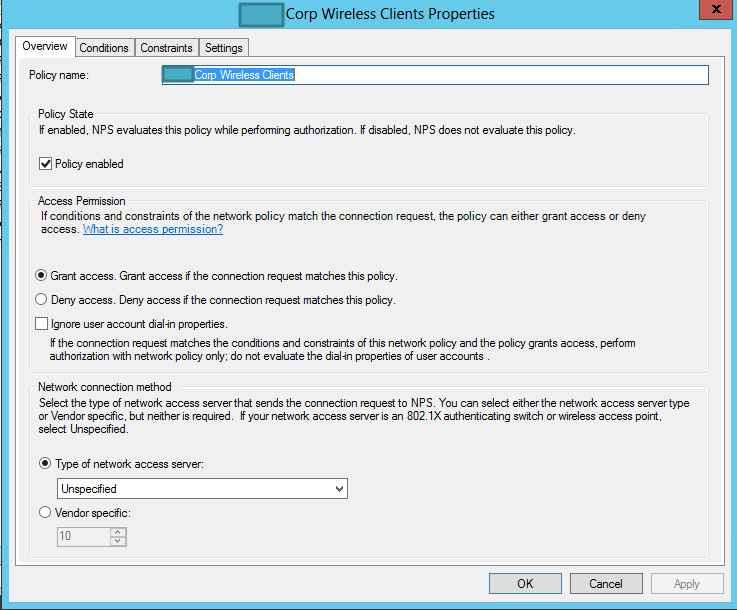
Give your Policy a meaningful name and make sure it’s enabled
For the Overview, make sure you check “Grant Access”, otherwise your clients will not connect. You don’t have to specify the network access server for this example.
Under Conditions, enter the IP of the Cisco WLC as an NAS IPv4 Address type. When IPv6 becomes available, you’ll see how this will change.
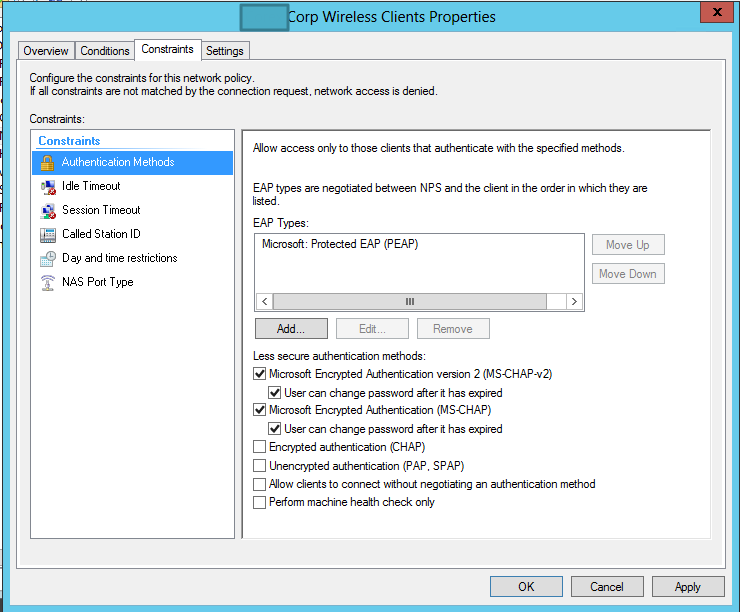
For Constraints, choose Authentication Methods, and add in Microsoft: Protected EAP (PEAP). Make sure it has the same checkmarks as the ones below:
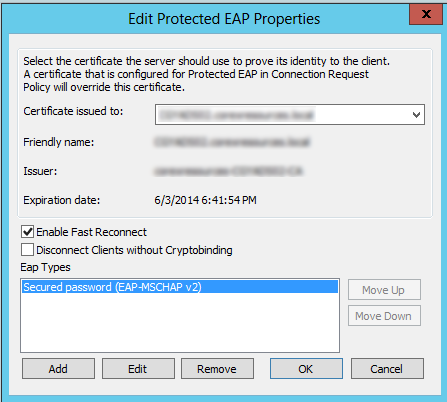
Highlight and click Edit… on the PEAP properties. Here is where you want to ensure you have the proper Certificate. Earlier in this tutorial, I mentioned using an RAS-IAS certificate over a domain issued certficate as the expiry date can be lengthened by a wider margin. In your dropdowns, you should see this one, and your domain certificate (if this is a domain server). If you’re having trouble deciding which certificate is which, Run the Windows Certification Authority and look at your issued certificates, the Certification path shows the name. Use the appropriate one you want. You should have only 1 option for EAP type: MSCHAP-V2.
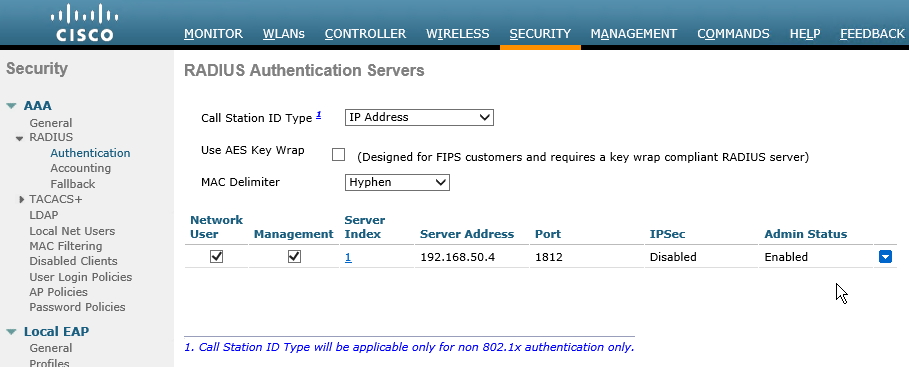
Next, log into your Wireless Lan Controller to do additional configuration. For this example, I’ve already created by Wireless network and given it an SSID (longer steps are involved for that of course). From the WLC main page, navigate to the Security Tab, and along the left hand side choose RADIUS->Authentication. Add a new Server Address, here I’ve plugged in the IP of my Windows NPS. Keep the default port 1812.
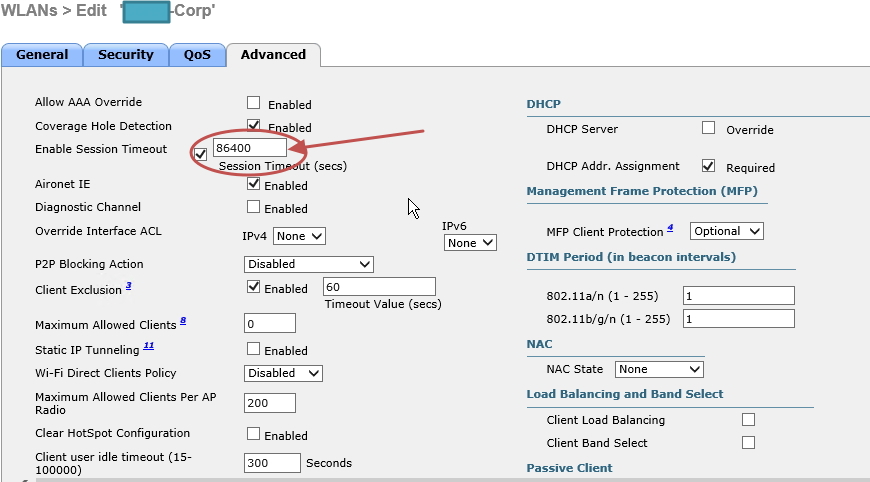
For my Cisco IOS version, I had to change my Session Time out value to 24 hours (86400 Seconds) as it was dropping every few minutes. Older Cisco IOS versions don’t have this issue- could be something to do with Server 2012 polling. Your mileage may vary.
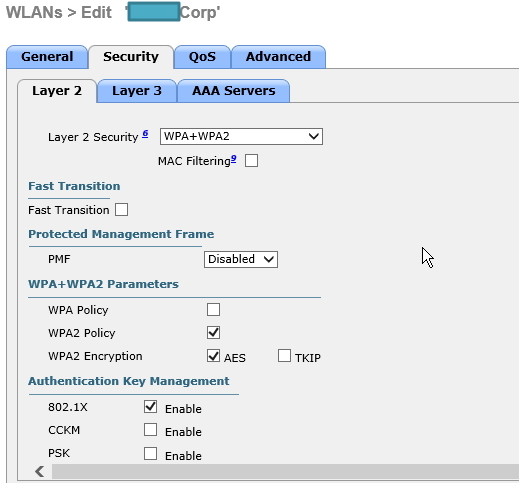
After adding in the IP of your NPS server, click on the SSID you want to use authentication, and choose the ‘Security’ Tab, in the sub tabs choose ‘Layer 2’, choose WPA+WPA2 for the type of security.
Next, choose ‘AAA Servers’. For the first server, it should populate to the IP of our NPS server we did in a previous step. The port will show up as 1812 (the default value) as well. Make sure to use LDAP authentication to the same server, or the IP address of your domain controller if your NPS lives elsewhere. Note the port changes for LDAP versus RADIUS NPS.